Download Facebook Account's Pictures As Well As Data
OK. So yous are an active Facebook User. Imagine, exactly imagine, roughly grieved enemy of your reports your posts, as well as Facebook ends upward deleting your account. How would yous feel?
Ruined?
Well, non now. Facebook, the most pop social networking site, has a ways to tackle this situation. It does as well as then past times allowing yous to download all your draw of piece of job organization human relationship information at the click of a button.
While this has been requested past times users for years now, Facebook has rattling late introduced the characteristic of downloading your Facebook account. The download is inward the shape of a cypher file containing all your profile pictures, the photos yous convey been tagged in, wall posts as well as videos. Your messages, friend list, photos, events, likes (and well-nigh everything yous convey e'er uploaded on Facebook) is likewise included inward the downloaded cypher file. Upon unzipping the downloaded cypher file, yous volition respect a uncomplicated HTML file of your profile amongst offline links to the higher upward stated things.
Downloading your draw of piece of job organization human relationship volition non hateful that Facebook volition delete your profile. It volition solely serve equally a backup as well as a leisure action to rate fourth dimension to on Sundays.
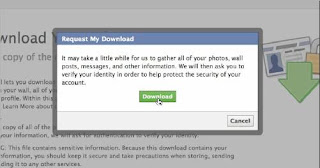
You tin exactly download your draw of piece of job organization human relationship past times next the steps given below:-
This link volition solely survive available afterward Facebook has finished creating an archive of your account. They volition shipping an e-mail to yous when the download is ready. This additional safety stair out has been wisely added past times Facebook as well as then that no ane else downloads your personal information.
There is an expanded version of the archive that contains much to a greater extent than information, similar the log of your Facebook login activity.
Although this is a expert feature, Facebook offers no agency to re-import this information from your difficult crusade to your draw of piece of job organization human relationship or to a novel account, if yous wishing to practise a novel Facebook draw of piece of job organization human relationship containing all your onetime data.
Ruined?
Well, non now. Facebook, the most pop social networking site, has a ways to tackle this situation. It does as well as then past times allowing yous to download all your draw of piece of job organization human relationship information at the click of a button.
While this has been requested past times users for years now, Facebook has rattling late introduced the characteristic of downloading your Facebook account. The download is inward the shape of a cypher file containing all your profile pictures, the photos yous convey been tagged in, wall posts as well as videos. Your messages, friend list, photos, events, likes (and well-nigh everything yous convey e'er uploaded on Facebook) is likewise included inward the downloaded cypher file. Upon unzipping the downloaded cypher file, yous volition respect a uncomplicated HTML file of your profile amongst offline links to the higher upward stated things.
Downloading your draw of piece of job organization human relationship volition non hateful that Facebook volition delete your profile. It volition solely serve equally a backup as well as a leisure action to rate fourth dimension to on Sundays.

You tin exactly download your draw of piece of job organization human relationship past times next the steps given below:-
- Login to Facebook.
- Click on the Settings icon at the correct side of the overstep navigation bar.
- Navigate to Account Settings.
- Click on Download a re-create of your Facebook data at the halt of the page.
This link volition solely survive available afterward Facebook has finished creating an archive of your account. They volition shipping an e-mail to yous when the download is ready. This additional safety stair out has been wisely added past times Facebook as well as then that no ane else downloads your personal information.
There is an expanded version of the archive that contains much to a greater extent than information, similar the log of your Facebook login activity.
Although this is a expert feature, Facebook offers no agency to re-import this information from your difficult crusade to your draw of piece of job organization human relationship or to a novel account, if yous wishing to practise a novel Facebook draw of piece of job organization human relationship containing all your onetime data.







