How To Honour A Phishing Email: An Example
Some of my of import emails destination upward inwards the Spam folder due to wrong filtering. So, I occasionally depository fiscal establishment lucifer the Spam folder to encounter if an e-mail that was non spam ended upward there. Today, spell checking the Spam folder, I came across an e-mail that was a classic trial of a phishing message. Hence, I decided to percentage it hither to betoken out roughly mutual tactics used inwards such messages.
Here is the email:-
One await at the from address should move plenty for anyone to guess that this message is non genuine. Messages from most companies are through a no-reply address. Also, most companies contact y'all from an e-mail address that is on their original domain, non roughly random costless e-mail provider. Moreover, almost all e-mail providers operate an interstitial page inwards the province of affairs described inwards this message. None of them sends an e-mail quest for verification.
Another of import affair to notice inwards this message is the Sent to: field. Notice how it mentions undisclosed recipients. This is mutual inwards such messages. They are sent to a lot of e-mail ids inwards i go. Hence, hiding the recipients allows hackers to foreclose their targets from knowing that this same message has been sent to a lot of users.
The side past times side affair to notice is that this message does non address me past times name. This is uncommon for an e-mail society that already has your name. Most companies add together the user's squall to add together a personalized feeling to their messages. This is something that is quite hard to care if y'all are sending the same message to thousands of users.
One of the most mutual characteristic of phishing emails is their operate of wrong grammar. This message is no different. The inappropriate capitalization in addition to spelling mistakes similar writing the give-and-take 'loosing' inwards house of 'losing' leaves no dubiety nearly its authenticity.
One to a greater extent than of import affair to notice is that at the destination of this message, in that place is no elevate of the e-mail provider's website. This is real uncommon considering that most e-mail providers larn out no rock unturned to build their messages.
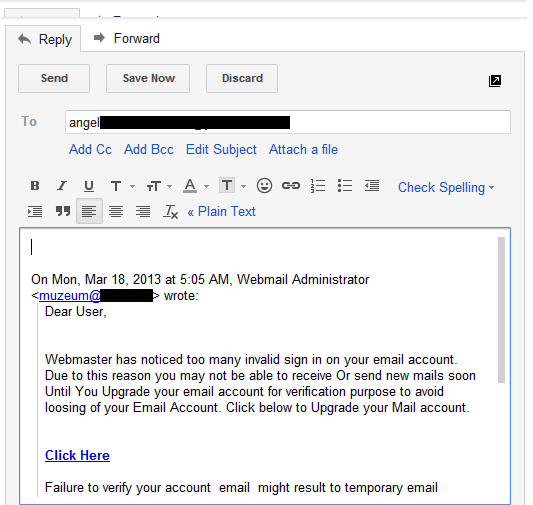
Lastly, the e-mail address to respond to is dissimilar from the i amongst which this message was sent. H5N1 proof that the sender of this message tried to spoof the sender id.
The techniques used inwards this e-mail were typical in addition to so it should non move hard for anyone to uncovering that it is a phishing message. However, cyber criminals are evolving in addition to most of them don't build such mutual mistakes anymore. You should ever operate mutual sense inwards such situations in addition to never click on suspicious links.
Here is the email:-
 |
| The phishing message. |
Another of import affair to notice inwards this message is the Sent to: field. Notice how it mentions undisclosed recipients. This is mutual inwards such messages. They are sent to a lot of e-mail ids inwards i go. Hence, hiding the recipients allows hackers to foreclose their targets from knowing that this same message has been sent to a lot of users.

The side past times side affair to notice is that this message does non address me past times name. This is uncommon for an e-mail society that already has your name. Most companies add together the user's squall to add together a personalized feeling to their messages. This is something that is quite hard to care if y'all are sending the same message to thousands of users.
One of the most mutual characteristic of phishing emails is their operate of wrong grammar. This message is no different. The inappropriate capitalization in addition to spelling mistakes similar writing the give-and-take 'loosing' inwards house of 'losing' leaves no dubiety nearly its authenticity.
One to a greater extent than of import affair to notice is that at the destination of this message, in that place is no elevate of the e-mail provider's website. This is real uncommon considering that most e-mail providers larn out no rock unturned to build their messages.

Lastly, the e-mail address to respond to is dissimilar from the i amongst which this message was sent. H5N1 proof that the sender of this message tried to spoof the sender id.
The techniques used inwards this e-mail were typical in addition to so it should non move hard for anyone to uncovering that it is a phishing message. However, cyber criminals are evolving in addition to most of them don't build such mutual mistakes anymore. You should ever operate mutual sense inwards such situations in addition to never click on suspicious links.