Lock A Folder Amongst Password Using Costless Folder Protector
All of us accept some files in addition to folders that nosotros visit private. They tin flame hold upwardly anything from our concern documents to pictures of friends in addition to family. These are files that nosotros don't desire other people using our figurer to know about. As Windows offers no agency to protect our somebody information, most of us become far awkward situations when these files are discovered past times unwanted people.
 Surely, yous tin flame shop this data inwards a hidden folder. The alone work is that anyone tin flame easily search the contents of a hidden folder using Windows Search itself.
Surely, yous tin flame shop this data inwards a hidden folder. The alone work is that anyone tin flame easily search the contents of a hidden folder using Windows Search itself.
The alone feasible solution is storing this content inwards a password protected folder in addition to then that alone those people knowing the password of the folder tin flame access it. There are many folder locking programs available online merely the work is that most of the proficient ones are paid. Even if yous create grapple to larn a proficient gratis one, yous volition hold upwardly looked at suspiciously when people come across a folder locker inwards the listing of your installed programs.
If yous besides abide by yourself inwards a similar situation, yous tin flame attempt Folder Protector, a password protector for Windows folders that is non alone gratis merely is also portable pregnant that it does non require to hold upwardly installed. Just click on the exe file in addition to the programme volition start running. I accept created this programme based on suggestions in addition to characteristic requests that I accept received past times e-mail over the terminal ii years.
Download for Windows XP
Important: 1) This programme uses a uncomplicated method to lock files in addition to should non hold upwardly used to protect genuinely sensitive information. It is best to encrypt that form of information.
2) Do non refresh your Windows PC when your folder is locked. Doing that volition delete your files.
How to purpose Folder Protector?
When yous run Folder Protector for the get-go time, the programme volition inquire yous for a password that yous desire to use. Enter a password that yous tin flame recollect every bit this volition hold upwardly the password to your protected folder.
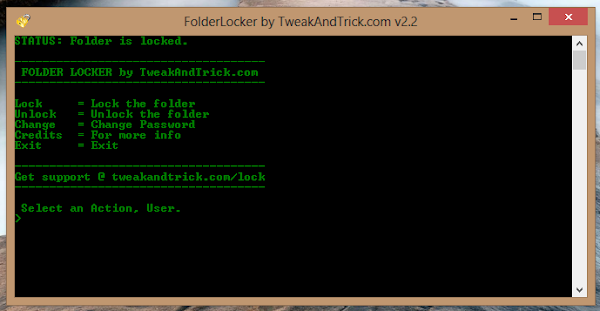
After entering the password, the programme volition opened upwardly a folder named SecuredFILES. This is your protected folder. You tin flame add together all your somebody files inwards this folder. This folder is located at the Desktop. After adding all your files, yous may closed this folder.
Then, yous tin flame purpose the bill of fare inwards the programme to lock your folder. To lock the folder, type lock every bit your action. After successfully locking the folder, FolderProtector volition display that the folder is locked.
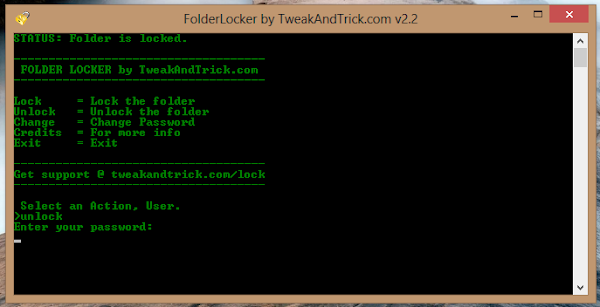
Unlocking the protected folder is easy. Just type unlock every bit your action. Then the programme volition inquire yous to larn inwards your password. Upon successfully entering the password, the programme volition display the contents of your protected folder.
Changing the Password: Just type alter every bit your action. The programme volition inquire yous for your electrical flow password. Upon successful entry of the electrical flow password, the programme volition inquire for your novel password in addition to alter it instantly.
Acknowledgment: This software has been made possible alone through the suggestions of readers of this blog, peculiarly Ernell Albert Galido for his see of using a bill of fare based interface.
Windows Compatibility: This programme has been successfully tested on Windows 10, Windows 8.1, Windows 8, Windows 7, Windows Vista in addition to Windows XP.
Support in addition to Development
I volition exceed away on to prepare this software further. So, your suggestions are invited. If yous human face upwardly whatever work acre using this software, yous tin flame purpose our support page.

The alone feasible solution is storing this content inwards a password protected folder in addition to then that alone those people knowing the password of the folder tin flame access it. There are many folder locking programs available online merely the work is that most of the proficient ones are paid. Even if yous create grapple to larn a proficient gratis one, yous volition hold upwardly looked at suspiciously when people come across a folder locker inwards the listing of your installed programs.
If yous besides abide by yourself inwards a similar situation, yous tin flame attempt Folder Protector, a password protector for Windows folders that is non alone gratis merely is also portable pregnant that it does non require to hold upwardly installed. Just click on the exe file in addition to the programme volition start running. I accept created this programme based on suggestions in addition to characteristic requests that I accept received past times e-mail over the terminal ii years.
Folder Protector
Folder Protector offers each user a protected folder that tin flame alone hold upwardly opened past times entering the password inwards FolderProtector. Unlike most safety programs, Folder Protector is pocket-size inwards size (nearly 58KB) in addition to does non demo the folder that it is protecting. This gives an additional payoff that people who don't know the password create non accept a target to attempt in addition to hack their agency into. As the this page, larn inwards the password in addition to access your protected files.Download Folder Protector
Download for Windows 10, 8, Windows seven in addition to Windows VistaDownload for Windows XP
Important: 1) This programme uses a uncomplicated method to lock files in addition to should non hold upwardly used to protect genuinely sensitive information. It is best to encrypt that form of information.
2) Do non refresh your Windows PC when your folder is locked. Doing that volition delete your files.
How to purpose Folder Protector?
When yous run Folder Protector for the get-go time, the programme volition inquire yous for a password that yous desire to use. Enter a password that yous tin flame recollect every bit this volition hold upwardly the password to your protected folder.

After entering the password, the programme volition opened upwardly a folder named SecuredFILES. This is your protected folder. You tin flame add together all your somebody files inwards this folder. This folder is located at the Desktop. After adding all your files, yous may closed this folder.
Then, yous tin flame purpose the bill of fare inwards the programme to lock your folder. To lock the folder, type lock every bit your action. After successfully locking the folder, FolderProtector volition display that the folder is locked.

Unlocking the protected folder is easy. Just type unlock every bit your action. Then the programme volition inquire yous to larn inwards your password. Upon successfully entering the password, the programme volition display the contents of your protected folder.
Changing the Password: Just type alter every bit your action. The programme volition inquire yous for your electrical flow password. Upon successful entry of the electrical flow password, the programme volition inquire for your novel password in addition to alter it instantly.
Acknowledgment: This software has been made possible alone through the suggestions of readers of this blog, peculiarly Ernell Albert Galido for his see of using a bill of fare based interface.
Windows Compatibility: This programme has been successfully tested on Windows 10, Windows 8.1, Windows 8, Windows 7, Windows Vista in addition to Windows XP.
Support in addition to Development
I volition exceed away on to prepare this software further. So, your suggestions are invited. If yous human face upwardly whatever work acre using this software, yous tin flame purpose our support page.