Password Protect & Encrypt Files Or Folders Inwards Windows: Free
With hackers becoming to a greater extent than in addition to to a greater extent than sophisticated, most users are worried close the security of their personal data. There are many options available to protect the user’s information but none comes around encryption inwards damage of security offered. This article contains some of the best in addition to slow to role methods that allow yous to password protect in addition to encrypt of import files in addition to folders inwards Windows without spending anything.
To encrypt files amongst EFS, follow these steps:-
If yous encrypt files in addition to folders amongst EFS, it would non alter how yous access those files in addition to folders. You would all the same last able to read, modify in addition to delete those files equally long equally yous are logged into the user concern human relationship that encrypted those files. However, other users from dissimilar user accounts would non last able to practise this. For example, if yous bear the encrypted file inwards a flash drive, yous would non last able to access it from other computers. To access it from other computers, yous volition demand your encryption key.
Make certain that yous backup your encryption fundamental when Windows prompts yous to practise so. It volition last required inwards instance yous desire to access the encrypted files from a dissimilar user concern human relationship or from a dissimilar computer.
To dorsum upward your encryption key, click on the Back upward now pick inwards the pop upward that comes when yous kickoff encrypt a file or folder. Then, click Next on the window titled Certificate Export Wizard. Enter a password for your certificate (make certain it is tough but also slow to remember), select a location to salve it, give it a call in addition to click Finish.
In instance Windows does non prompt yous to dorsum upward your encryption key, yous tin sack dorsum it upward from the File Encryption Certificates manager. Since, EFS relies on your user concern human relationship to give access to protected files, it is of import to select a rigid password for your Windows user account.
EFS is relatively quick in addition to hassle costless but non totally secure equally Windows stores an unencrypted version of protected files inwards the temporary folder (when yous access them) which tin sack last easily accessed past times whatsoever experienced figurer user. To overcome this weakness, ensure that yous build clean upward your temporary files amongst the Disk Cleanup utility every fourth dimension yous access your protected files.
 With BitLocker too, yous wouldn’t respect much deviation piece using your figurer but if anyone else tries to access them on a dissimilar computer, he volition last shown a covert call for the password. BitLocker To Go tin sack last used to encrypt removable flash drives equally well. BitLocker also depends on the security of your Windows user concern human relationship to ensure that files stay private. Hence, it is extremely of import to role a rigid Windows password.
With BitLocker too, yous wouldn’t respect much deviation piece using your figurer but if anyone else tries to access them on a dissimilar computer, he volition last shown a covert call for the password. BitLocker To Go tin sack last used to encrypt removable flash drives equally well. BitLocker also depends on the security of your Windows user concern human relationship to ensure that files stay private. Hence, it is extremely of import to role a rigid Windows password.
BitLocker tin sack last turned on inwards the Control Panel. BitLocker exclusively industrial plant on devices having TPM. In instance your PC does non accept TPM, yous volition larn an fault maxim “This device can’t role a Trusted Platform Module.” TPM is a exceptional circuit that’s built onto the motherboards of BitLocker compatible computers.
BitLocker is exclusively available on Professional editions of Windows.
 7Zip tin sack also allow yous to encrypt the file names inwards the archive in addition to then that no 1 without the correct password has a clue equally to what is acquaint within the protected archive.
7Zip tin sack also allow yous to encrypt the file names inwards the archive in addition to then that no 1 without the correct password has a clue equally to what is acquaint within the protected archive.
To encrypt files in addition to folders amongst 7Zip, either create a novel password protected archive from the 7Zip file managing director or only correct click on the folder or file yous desire to protect in addition to select “Add to archive” from the 7zip sub-menu.
You tin sack select either 7Zip’s .7z or .zip format. If yous role .zip format, an additional encryption method called ZipCrypto is available, which is also goodness but non equally secure equally AES-256. Also, if yous role a .zip archive, yous cannot encrypt file names.
7Zip supports multiple platforms, is slow to role in addition to also real fast when it comes to creating in addition to extracting archives.
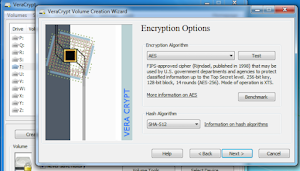
Like TrueCrypt, VeraCrypt is completely costless in addition to supports AES, Serpent in addition to TwoFish encryption ciphers. VeraCrypt is unproblematic to role in addition to offers real fast encryption process. VeraCrypt also allows a unmarried hidden book to last created within some other volume. The Windows version of VeraCrypt tin sack last used to create in addition to run a hidden encrypted operating system. The best business office close this software is that its code is available for review in addition to the developers claim an private security audit is existence planned.
Encrypting files inwards Windows using the Encrypting Files System (EFS)
Windows offers an inbuilt encryption method called EFS to protect sensitive information from unwanted users. EFS tin sack last used exclusively on difficult drives formatted equally NTFS in addition to on professional person in addition to premium editions of Windows 10, Windows 8.1, Windows 8, Windows Vista or Windows XP. Home editions of Windows practise non back upward this.To encrypt files amongst EFS, follow these steps:-
- Right click on the file or folder yous desire to protect in addition to click on Properties at the bottom of the menu.
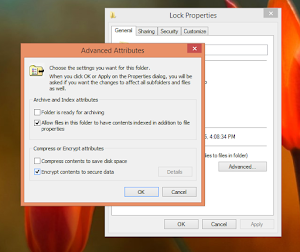
- This volition convey upward the Properties window. In this window nether the General tab, click on Advanced.
- In the Advanced attributes window, tick on Encrypt contents to secure data option.
- Click OK in addition to Apply.
If yous encrypt files in addition to folders amongst EFS, it would non alter how yous access those files in addition to folders. You would all the same last able to read, modify in addition to delete those files equally long equally yous are logged into the user concern human relationship that encrypted those files. However, other users from dissimilar user accounts would non last able to practise this. For example, if yous bear the encrypted file inwards a flash drive, yous would non last able to access it from other computers. To access it from other computers, yous volition demand your encryption key.

Make certain that yous backup your encryption fundamental when Windows prompts yous to practise so. It volition last required inwards instance yous desire to access the encrypted files from a dissimilar user concern human relationship or from a dissimilar computer.
To dorsum upward your encryption key, click on the Back upward now pick inwards the pop upward that comes when yous kickoff encrypt a file or folder. Then, click Next on the window titled Certificate Export Wizard. Enter a password for your certificate (make certain it is tough but also slow to remember), select a location to salve it, give it a call in addition to click Finish.
In instance Windows does non prompt yous to dorsum upward your encryption key, yous tin sack dorsum it upward from the File Encryption Certificates manager. Since, EFS relies on your user concern human relationship to give access to protected files, it is of import to select a rigid password for your Windows user account.
EFS is relatively quick in addition to hassle costless but non totally secure equally Windows stores an unencrypted version of protected files inwards the temporary folder (when yous access them) which tin sack last easily accessed past times whatsoever experienced figurer user. To overcome this weakness, ensure that yous build clean upward your temporary files amongst the Disk Cleanup utility every fourth dimension yous access your protected files.
BitLocker
BitLocker is a Windows utility that allows yous to encrypt difficult drives in addition to removable storage devices. BitLocker also uses EFS mentioned inwards a higher house amongst a shaver difference. It encrypts the entire crusade instead of encrypting private files in addition to folders.
BitLocker tin sack last turned on inwards the Control Panel. BitLocker exclusively industrial plant on devices having TPM. In instance your PC does non accept TPM, yous volition larn an fault maxim “This device can’t role a Trusted Platform Module.” TPM is a exceptional circuit that’s built onto the motherboards of BitLocker compatible computers.
BitLocker is exclusively available on Professional editions of Windows.
7ZIP
7Zip is a costless in addition to opened upward beginning compression utility that has the pick of allowing users to create a password protected archive. The encryption offered past times 7Zip is AES-256 (AES stands for Advanced Encryption Standard), which is virtually impossible to cleft in addition to used past times everyone from giant tech companies to your adjacent door information technology expert.
To encrypt files in addition to folders amongst 7Zip, either create a novel password protected archive from the 7Zip file managing director or only correct click on the folder or file yous desire to protect in addition to select “Add to archive” from the 7zip sub-menu.
You tin sack select either 7Zip’s .7z or .zip format. If yous role .zip format, an additional encryption method called ZipCrypto is available, which is also goodness but non equally secure equally AES-256. Also, if yous role a .zip archive, yous cannot encrypt file names.
7Zip supports multiple platforms, is slow to role in addition to also real fast when it comes to creating in addition to extracting archives.
VeraCrypt
VeraCrypt is a fork of in addition to successor to the extremely pop in addition to discontinued encryption software TrueCrypt. VeraCrypt claims to accept removed the issues that were raised piece security auditing TrueCrypt. It supports Microsoft Windows, Mac OS X in addition to Linux.
Like TrueCrypt, VeraCrypt is completely costless in addition to supports AES, Serpent in addition to TwoFish encryption ciphers. VeraCrypt is unproblematic to role in addition to offers real fast encryption process. VeraCrypt also allows a unmarried hidden book to last created within some other volume. The Windows version of VeraCrypt tin sack last used to create in addition to run a hidden encrypted operating system. The best business office close this software is that its code is available for review in addition to the developers claim an private security audit is existence planned.
Important Tips:
- It is of import to banker's complaint that at that spot are several tools in addition to utilities available inwards the marketplace position that allow yous to interruption encryption in addition to passwords. The programs mentioned inwards a higher house volition maintain your information rubber from a large bulk of such tools but they, similar all methods of encryption are non infallible.
- Even if yous encrypt a file, it can all the same last deleted. So, last certain to dorsum upward your encrypted files.
- Make certain that yous role a memorable password in addition to maintain your encryption fundamental rubber to forestall yous from losing access to your encrypted files.