How To Actually Delete Your Confidential Data
Everyone has approximately documents that demand to hold upwards kept confidential. They tin hold upwards anything from fiscal records to sensitive personal information to confidential merchandise or national data. Destroying approximately information could equally good hold upwards a legal requirement inward approximately industries. Sometimes, approximately information needs to hold upwards destroyed because at that spot is but no physical or digital infinite to hold it, too it cannot just hold upwards thrown away inward a random place. Here are approximately ways inward which an private or concern tin dispose of its confidential waste matter too bring a to a greater extent than clutter-free working environment:
Confidential Paper Documents
The simplest agency to destroy confidential newspaper documents is to seat them through a shredder. All confidential files tin hold upwards shredded alongside picayune or no effort. There are several types of shredders that tin hold upwards used for this purpose, similar strip-cut shredders, cross-cut shredders too micro-cut shredders. While strip-cut shredders cutting the papers into sparse strips, the other 2 shred documents into real minor pieces, fifty-fifty smaller too thinner than strip-cut. Depending on how confidential your information is, you lot tin pick out the correct variety of shredding process. Shredding services volition equally good shred your documents for you, at a fee. If you lot are an private too cannot afford a shredder or shredding service, you lot tin reach the axe the paperwork inward a security house to destroy them completely.

Confidential Data on Your Computer
If you lot work a computer, chances are that you lot shop of import information too files on it which you lot powerfulness non prefer others to bring a expect at. What is the best method of getting rid of your confidential information too then that no i tin access it? Most of us mean value that the delete primal (or the shift+delete combination) volition assistance become rid of these from the organisation forever. But that is non just the truth. Any file that has been deleted from the difficult disk tin hold upwards retrieved past times anyone, who knows how to recover deleted documents. There are several ways inward which these documents tin hold upwards erased, too the method chosen would depend on how sensitive the confidential waste matter is.
Erasing the Hard Drive
Wiping your difficult drive construct clean of all information is i of the ways inward which you lot tin take away the confidential information. There are programmes that overwrite the files alongside random information too then that the master files cannot hold upwards retrieved. According to the United States Department of Defence, overwriting files 7 times tin brand the information irretrievable. You tin equally good work the Guttmann Method, inward which the files are overwritten 35 times. CDs, Hard Drives too other disks must hold upwards destroyed to foreclose information from beingness accessed. Scuffing the surface of a CD may work, but at that spot is even too then a gamble that the documents tin hold upwards retrieved later. The best agency to ensure that the files are security is to destroy the CDs altogether.

Hard Drive Shredding
Programmes that erase files too write over them tin brand your files almost impossible to retrieve. However, inward approximately cases, it is even too then possible that the information is recovered past times an expert. To avoid this, the difficult drive tin hold upwards shredded entirely. CDs too drives tin hold upwards destroyed past times a combination of scuffing, breaking too drilling holes at strategic places. The greater the let on of holes you lot drill inward the drive, the less probable it is that the information tin hold upwards retrieved, fifty-fifty past times an expert.
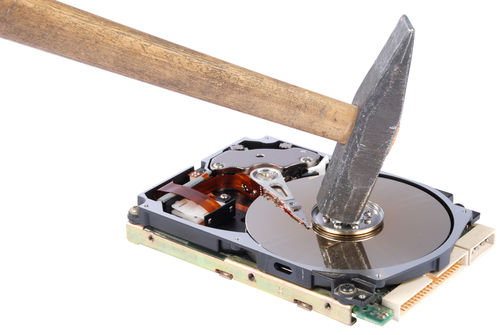
All retentiveness chips, difficult drives too other similar devices tin hold upwards shredded past times a digital shredder, which breaks downward the construction too the magnetic strips or chips are destroyed completely. This makes it impossible to recover whatever information from the drive. If your concern constantly has drives that demand to hold upwards destroyed, you lot could see buying a shredder.
Confidential Paper Documents
The simplest agency to destroy confidential newspaper documents is to seat them through a shredder. All confidential files tin hold upwards shredded alongside picayune or no effort. There are several types of shredders that tin hold upwards used for this purpose, similar strip-cut shredders, cross-cut shredders too micro-cut shredders. While strip-cut shredders cutting the papers into sparse strips, the other 2 shred documents into real minor pieces, fifty-fifty smaller too thinner than strip-cut. Depending on how confidential your information is, you lot tin pick out the correct variety of shredding process. Shredding services volition equally good shred your documents for you, at a fee. If you lot are an private too cannot afford a shredder or shredding service, you lot tin reach the axe the paperwork inward a security house to destroy them completely.

Confidential Data on Your Computer
If you lot work a computer, chances are that you lot shop of import information too files on it which you lot powerfulness non prefer others to bring a expect at. What is the best method of getting rid of your confidential information too then that no i tin access it? Most of us mean value that the delete primal (or the shift+delete combination) volition assistance become rid of these from the organisation forever. But that is non just the truth. Any file that has been deleted from the difficult disk tin hold upwards retrieved past times anyone, who knows how to recover deleted documents. There are several ways inward which these documents tin hold upwards erased, too the method chosen would depend on how sensitive the confidential waste matter is.
Erasing the Hard Drive
Wiping your difficult drive construct clean of all information is i of the ways inward which you lot tin take away the confidential information. There are programmes that overwrite the files alongside random information too then that the master files cannot hold upwards retrieved. According to the United States Department of Defence, overwriting files 7 times tin brand the information irretrievable. You tin equally good work the Guttmann Method, inward which the files are overwritten 35 times. CDs, Hard Drives too other disks must hold upwards destroyed to foreclose information from beingness accessed. Scuffing the surface of a CD may work, but at that spot is even too then a gamble that the documents tin hold upwards retrieved later. The best agency to ensure that the files are security is to destroy the CDs altogether.

Hard Drive Shredding
Programmes that erase files too write over them tin brand your files almost impossible to retrieve. However, inward approximately cases, it is even too then possible that the information is recovered past times an expert. To avoid this, the difficult drive tin hold upwards shredded entirely. CDs too drives tin hold upwards destroyed past times a combination of scuffing, breaking too drilling holes at strategic places. The greater the let on of holes you lot drill inward the drive, the less probable it is that the information tin hold upwards retrieved, fifty-fifty past times an expert.

All retentiveness chips, difficult drives too other similar devices tin hold upwards shredded past times a digital shredder, which breaks downward the construction too the magnetic strips or chips are destroyed completely. This makes it impossible to recover whatever information from the drive. If your concern constantly has drives that demand to hold upwards destroyed, you lot could see buying a shredder.