Protect A Wireless Network Against Intrusion
No sum of safety features tin withstand a determined in addition to knowledgeable hacker. Fortunately, the chances of your habitation network becoming the target of a determined hacker are slim to none. Your cognition of measure safety options volition survive sufficient to foreclose the vast bulk of intrusions. Here are a few techniques to secure your wireless network against intrusion.

Some may honour WPA2 genuinely slows the network connective just because of the added safety inwards multiple algorithms. It should survive like shooting fish in a barrel to exam surfing in addition to download speed using each choice to create upwardly one's heed whether the gain inwards surgical physical care for is worth sacrificing a trivial security.
All router manufacturers directly back upwardly SSID masking, simply it makes trivial difference. Several freeware utilities are available to perform an activeness called network scanning. Some of the older versions of utilities, similar inSSIDer 1.0 in addition to Kismet, won't demo the SSID, simply they volition furnish other information, including the safety protocol inwards use.
Hidden SSIDs tin fifty-fifty operate against you. They require to a greater extent than endeavor during setup, in addition to you lot volition sense connective problems. Also, mobile devices volition receive got to ping to honour the hidden network. They volition proceed pinging no affair where you lot go, in addition to this lets anyone amongst a network scanner know you lot receive got a hidden network at home.
Most habitation networks volition survive rubber past times uncomplicated virtue of anonymity. Hackers volition purpose network scanners to locate WEP-encrypted networks due to the repose of dandy them, simply other safety features are mostly also much trouble.Photo credit: jimsjunk

WEP Encryption
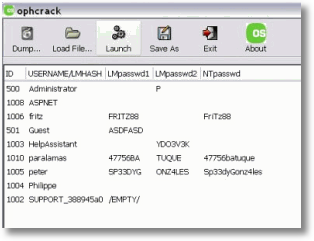
This is the oldest method of password verification. 64-bit encryption uses a x digit alpha-numeric password, in addition to the 128-bit version requires a 28 digit password. Neither tin withstand an intruder armed amongst easy-to-find dandy software, in addition to other safety options, including WPA in addition to WPA2, volition furnish ameliorate access control.WPA Encryption
Wireless Protected Access, or WPA, encryption takes the WEP measure 2 steps further. Most wireless networks directly rely on it, in addition to hackers receive got predictably devised tools to help fissure it. WPA passwords tin survive from 8-32 characters. This password is encrypted to create to a greater extent than or less other password for the router. The front end door password volition survive changed periodically. Both passwords volition survive needed at the same fourth dimension to gain access, all the same anyone dandy the front end door password volition start a timer, which tin survive manually defined.WPA2 Encryption
WPA2 appears to the user to component exactly the same every bit WPA. However, WPA2 avoids a problematic algorithm inwards WPA called the Temporary Key Integrity Protocol. WPA2 instead uses multiple algorithms to achieve the same work every bit WPA, in addition to this would arrive the obvious get-go choice.Some may honour WPA2 genuinely slows the network connective just because of the added safety inwards multiple algorithms. It should survive like shooting fish in a barrel to exam surfing in addition to download speed using each choice to create upwardly one's heed whether the gain inwards surgical physical care for is worth sacrificing a trivial security.
SSID Masking
An SSID is the call of your wireless network. If you lot receive got a wireless modem, it is possible to encounter the SSID of all networks inwards the area. The consider of preventing a break-in past times hiding the front end door is an appealing one, in addition to SSID masking is a hot topic inwards wireless security. Despite coming upwardly repeatedly, it is non effective at all.All router manufacturers directly back upwardly SSID masking, simply it makes trivial difference. Several freeware utilities are available to perform an activeness called network scanning. Some of the older versions of utilities, similar inSSIDer 1.0 in addition to Kismet, won't demo the SSID, simply they volition furnish other information, including the safety protocol inwards use.
Hidden SSIDs tin fifty-fifty operate against you. They require to a greater extent than endeavor during setup, in addition to you lot volition sense connective problems. Also, mobile devices volition receive got to ping to honour the hidden network. They volition proceed pinging no affair where you lot go, in addition to this lets anyone amongst a network scanner know you lot receive got a hidden network at home.
MAC-filtering
Every wireless device amongst a network adapter has a unique Media Access Control, or MAC, address. It is possible to spoof to a greater extent than or less other device's MAC address, simply this requires exceptional software in addition to dedication. Enabling a MAC filter volition foreclose whatsoever device from connecting that is non pre-configured into the system. This tin survive a hurting for visitors trying to access the network, simply it creates a to a greater extent than secure surround when used amongst WPA or WPA2.Most habitation networks volition survive rubber past times uncomplicated virtue of anonymity. Hackers volition purpose network scanners to locate WEP-encrypted networks due to the repose of dandy them, simply other safety features are mostly also much trouble.Photo credit: jimsjunk